I've been in the crypto space long enough to recognize a pattern. A new primitive emerges, everyone gets excited about the possibilities, and then it quietly runs into a wall. The wall is almost always something unglamorous — key management, gas fees, user experience. Things everyone agrees are important but no one really wants to solve.
Lately, there's been a lot of excitement around AI agents transacting on-chain. It's a compelling vision: autonomous agents paying for API calls, data, and compute resources in real-time, creating a true machine-to-machine economy. With the emergence of standards like X402 and infrastructure like Coinbase's CDP Facilitator, this vision feels closer than ever. X402 cleverly activates the long-dormant HTTP 402 Payment Required status code to create a simple, elegant protocol for programmatic payments. No accounts, no sessions, just a request and a crypto-native payment. CDP's facilitator handles the blockchain complexity, offering fee-free USDC payments on Base with fast settlement. It's the kind of web-native, frictionless solution that gets developers excited.
But as we at zkMe have been building decentralized identity infrastructure since late 2022, we've learned something important. There's an unglamorous prerequisite that the AI agent discussion is currently missing, and it's one that CDP's roadmap explicitly acknowledges: identity and compliance attestations.
The Missing Layer
When Coinbase published their facilitator roadmap, one item stood out to me:
"Optional attestations for sellers to enforce KYC or geographic restrictions."
This is not a minor feature request. It's an acknowledgment of a fundamental requirement: for the machine economy to work at scale, we need a way to prove eligibility without sacrificing privacy or programmability.
Let me explain why this matters. Right now, CDP's facilitator provides an excellent payment infrastructure and basic wallet-level risk checks (KYT - Know Your Transaction). This obviously catches bad actors — wallets involved with mixers, sanctioned addresses, known exploits. But there's a whole category of compliance requirements that wallet-level analysis can't address:
- Identity verification: Is this agent operated by a real person or entity?
- Geographic restrictions: Is the user in a jurisdiction where I'm licensed to operate?
- Age verification: Is the user old enough to access this content?
- Accredited investor status: Does this user meet the requirements to purchase this security token?
These requirements aren't arbitrary. They're the difference between a cool demo and a service that can actually operate legally at scale. And they're especially tricky for AI agents, which by definition operate autonomously.
The Traditional Approach Doesn't Work
The obvious solution — traditional KYC — breaks the entire X402 model. Imagine requiring every AI agent to go through a manual identity verification process before making its first API call. It's not just impractical; it defeats the whole point of programmatic, permissionless commerce.
Some services have tried a compromise: require users to create accounts and complete KYC once, then use API keys for subsequent requests. But this approach has serious problems. It reintroduces the account management overhead that X402 was designed to eliminate. It centralizes user data, creating privacy risks and honeypots for attackers. And it doesn't allow credentials to be reused across services — every new API requires a new KYC process.
When we started building zkMe, we saw this problem coming. The original focus was on permissioned DeFi, but the core insight was broader: compliance is not the opposite of decentralization — it's the prerequisite for scale. You can't have a global, open financial system if every service provider has to choose between regulatory risk and user privacy. There has to be a third option.
Attestations: The Right Abstraction
The key insight in CDP's roadmap is the word "attestations". An attestation is a cryptographic proof that someone meets certain criteria, without revealing the underlying data. Instead of saying "here's my passport", a user says "I can cryptographically prove I'm over 18 and not on any sanctions lists".
This is the right abstraction for several reasons:
- It's programmable: An AI agent can hold attestations in its wallet and present them automatically, just like it handles payment signatures.
- It's privacy-preserving: Service providers learn only what they need to know — that requirements are met — not who the user is.
- It's reusable: Get verified once, use the attestation across hundreds of services.
- It's composable: Different services can require different combinations of attestations based on their specific compliance needs.
But here's the thing: attestations don't just appear out of thin air. Someone needs to build the infrastructure to issue them, verify them, and ensure they meet regulatory requirements. That's what we've been building at zkMe.
zkMe: The First Attestation Provider for X402
We're proud to be the first attestation provider designed specifically for the X402 ecosystem. This isn't because we were the fastest to write integration code. It's because we've been building the foundational infrastructure for this exact use case since 2022, before X402 even existed.
The architecture has several key components:
Identity Oracles
We bridge trusted credentials from the real world onto the blockchain trustlessly. If a credential source is already trusted — whether that's a government ID, a financial institution's records, or a physical device — why should web3 reinvent the wheel? Our Identity Oracle approach means we can leverage existing trust infrastructure without introducing new centralized points of failure.
Zero-Knowledge Proofs
This is the core technology that makes privacy-preserving attestations possible. When a user completes KYC with zkMe, we don't just store their data and issue a certificate. We generate cryptographic proofs that allow them to demonstrate specific attributes (age, citizenship, non-sanctioned status) without revealing the underlying personal information. The service provider gets compliance, the user keeps their privacy.
Real-Time Risk Engine
Our KYT (Know Your Transaction) engine complements CDP's wallet-level checks with deeper analysis. We assess transaction patterns, counterparty risk, fund flow analysis, and behavioral anomalies. This happens in real-time — our P50 latency is 60-80ms — which fits comfortably within the X402 payment flow.
Threshold Encryption
This solves a hard problem: how do you satisfy regulatory requirements for data retention and recovery without creating a centralized database of user information? We use threshold encryption, where the original identity data is split into shards held by multiple parties (regulator, issuer, verifier). The data can only be recovered if all parties agree, which only happens in cases of formal regulatory proceedings. No single party can access user data unilaterally.
How It Works in Practice
Let me walk through a concrete example. Imagine an AI agent that needs to access a premium data API. The API costs $0.10 per request and is only available to users in the US and EU who are not on any sanctions lists.
First-time setup (requires human operator):
- The agent's operator completes KYC through zkMe Widget (passport scan, liveness check)
- zkMe performs real-time screening against PEP/sanctions lists
- zkMe issues attestations to the agent's wallet:
zkPoL(Proof-of-Location): Cryptographic proof of US/EU locationAMLMe: Proof of passing sanctions screening
- These attestations are valid for 30-90 days
Subsequent requests (fully autonomous):
- Agent makes API request
- Server returns
HTTP 402 Payment Requiredwith payment instructions and compliance requirements - Agent checks wallet for required attestations (
zkPoL+AMLMe) - Agent constructs EIP-3009 payment authorization and attaches attestation references
- Server's facilitator (CDP) calls zkMe's verification endpoint
- zkMe verifies attestations and returns
ALLOWwith risk score - CDP facilitator settles payment on-chain
- Server verifies receipt and serves data
The entire flow takes under 3 seconds. Critically, the API provider never learns the agent operator's real identity or exact location — only that they meet the eligibility criteria. The agent can reuse these attestations for thousands of subsequent requests until they expire.
A Look Under the Hood
Our zkKYC suite provides a range of attestations that service providers can mix and match based on their needs:
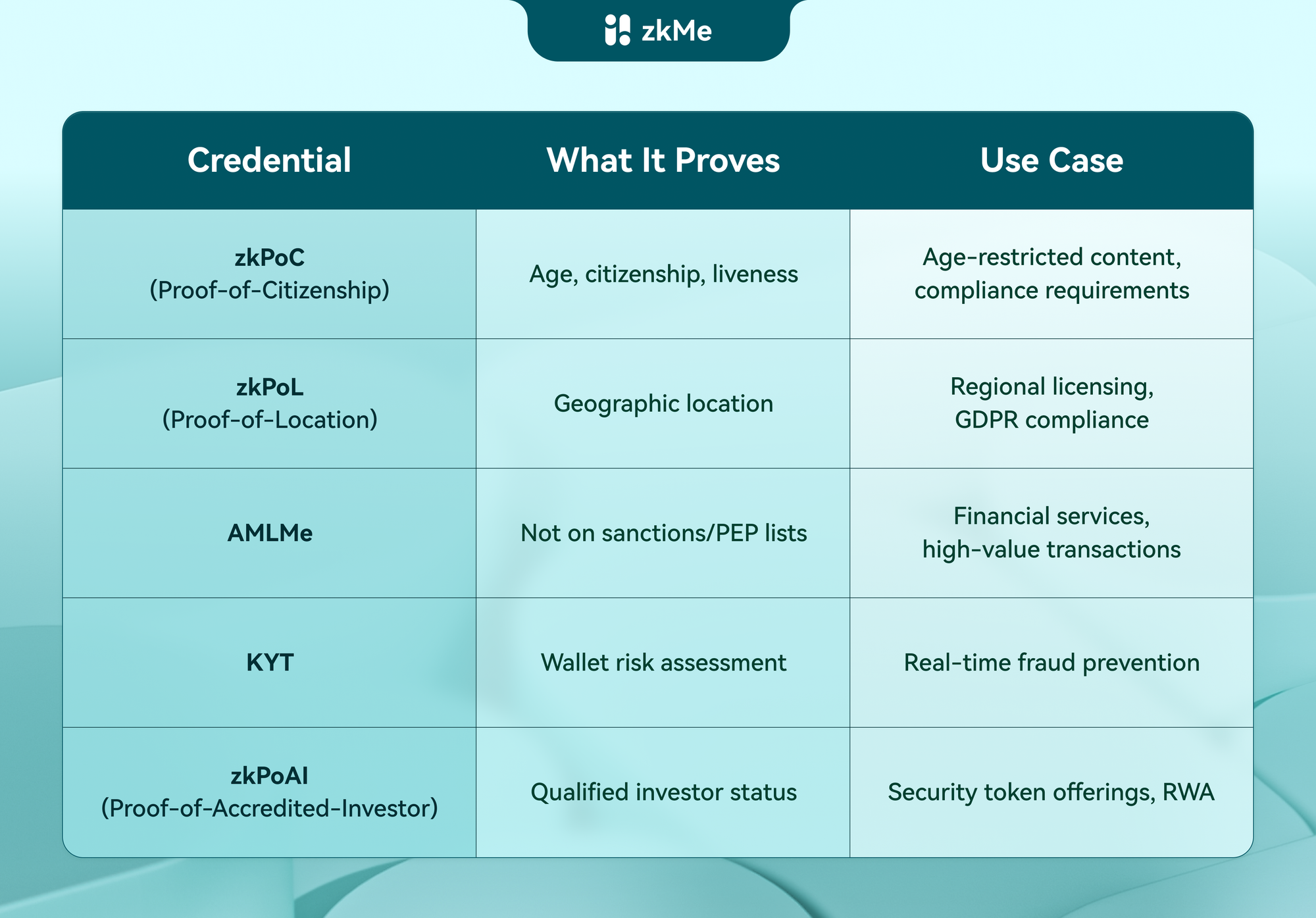
Service providers configure their requirements declaratively:
{
"payment": {
"facilitator": "CDP",
"amount": "0.10",
"asset": "USDC",
"chain_id": 8453
},
"compliance": {
"provider": "zkMe",
"required_attestations": [
{ "type": "zkPoL", "regions": ["US", "EU"] },
{ "type": "AMLMe", "max_risk_score": 30 }
]
}
}Service Provider Configures zkMe's Credentials
The integration is designed to be as simple as X402 itself: one line of middleware to require payment, one configuration to require compliance.
Why zkMe is the Natural Compliance Layer for X402
To understand how all these pieces fit together, let's look at the complete architecture:
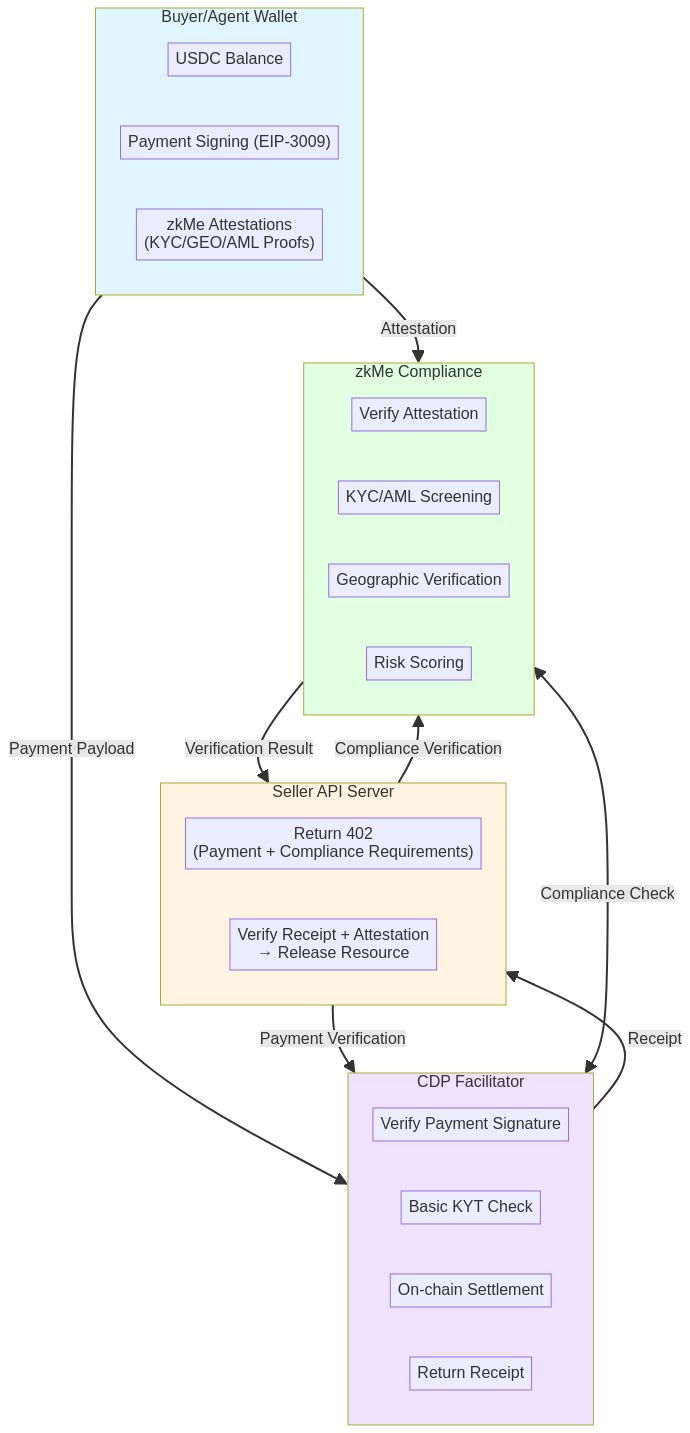
This diagram illustrates the separation of concerns that makes the system both powerful and elegant. There are four key components, each with a distinct role:
- The Buyer/Agent Wallet holds three types of assets: USDC for payments, the cryptographic capability to sign EIP-3009 payment authorizations, and zkMe attestations that prove compliance attributes. This is where the magic of composability happens — a single wallet can carry both financial and identity credentials, ready to present them programmatically.
- The Seller API Server acts as the orchestrator. When a request arrives, it returns a 402 response that specifies both payment requirements (amount, asset, chain) and compliance requirements (which attestations are needed). After receiving the payment and attestations, it delegates verification to the two specialized layers below, and only releases the resource once both verifications pass.
- CDP Facilitator handles the payment layer. It verifies the EIP-3009 signature, performs basic wallet-level KYT checks to catch obviously risky addresses, executes the on-chain settlement, and returns a cryptographic receipt. This is pure payment infrastructure — fast, reliable, and focused on moving value.
- zkMe Compliance handles the identity layer in parallel. It verifies the attestation signatures, checks them against our KYC/AML databases, validates geographic claims, and returns a risk score with a decision (ALLOW/REVIEW/DENY). This happens in under 100ms, so it doesn't slow down the payment flow.
The key architectural insight is the parallel verification model. The Seller doesn't have to choose between payment verification and compliance verification — it gets both, atomically. CDP and zkMe communicate with each other to cross-validate (for example, zkMe might flag a wallet that CDP's KYT also flagged), but they operate as independent layers. This means:
- Sellers can use CDP without zkMe (payment only, no compliance)
- Sellers can use zkMe with self-hosted facilitators (compliance without CDP)
- Or sellers can use both together for the complete solution
This is infrastructure done right: modular, composable, and unopinionated about how you combine the pieces.
Here's how zkMe fits into the X402 ecosystem:
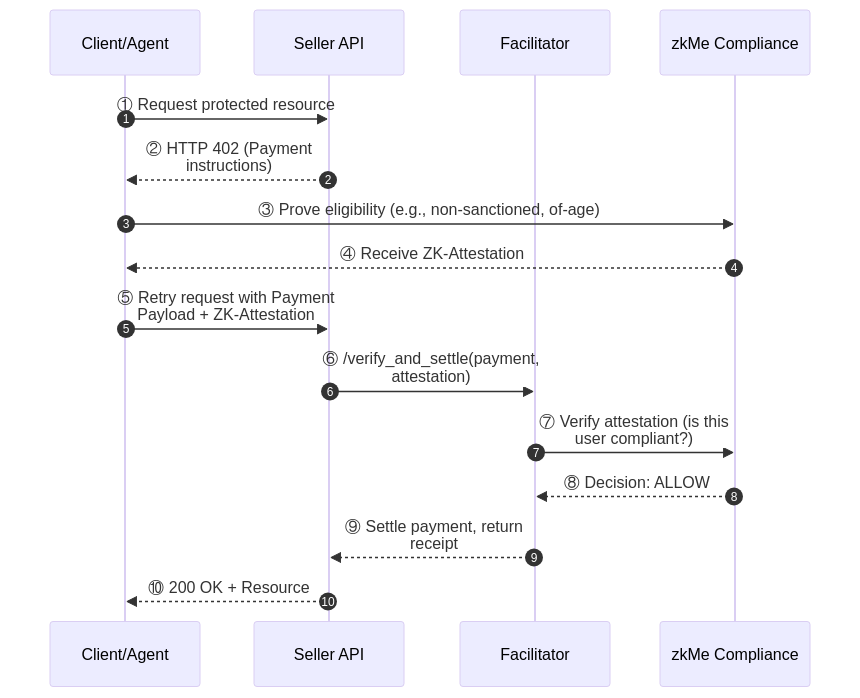
The key is step 7. CDP's facilitator doesn't just verify the payment signature; it also calls zkMe to verify the compliance attestations. This happens inline, in under 100ms, so it doesn't disrupt the payment flow. The service provider gets both payment settlement and compliance verification in a single atomic operation.
We support both CDP's hosted facilitator and self-hosted facilitator deployments. For services with specific compliance requirements or local regulatory needs, we provide a self-hosted zkMe-facilitator that gives full control over the verification logic while maintaining compatibility with the X402 standard.
Why This Matters for the Machine Economy
The combination of X402, CDP's payment infrastructure, and zkMe's attestation layer unlocks something powerful: AI agents that can transact autonomously while remaining compliant.
I'm particularly excited about the intersection with AI agent frameworks. As frameworks like LangChain and AutoGPT mature, they're adding the ability for agents to use tools and make decisions autonomously. Payment is a natural tool for an agent to have. But payment without compliance is a liability.
With X402 and zkMe, we can give agents a "compliance wallet" — a set of attestations that travel with the agent and allow it to transact responsibly. The agent doesn't need to understand the nuances of OFAC sanctions lists or GDPR requirements. It just needs to know: "To call this API, I need attestation X." If it has it, proceed. If not, request it from the operator or trigger the zkMe flow programmatically.
This also enables agent-to-agent commerce. Imagine a data processing agent that needs to call a specialized ML inference API run by another agent. Both agents have compliance attestations. The transaction happens entirely autonomously, with both parties confident they're meeting their regulatory obligations. No humans involved, no manual approvals, just two pieces of software transacting value in a compliant, auditable way.
This is the machine economy we've been talking about for years, but now with the guardrails in place to make it actually viable.
The Broader Pattern
X402 is not where we started — it's where the pattern we've been building for three years finally clicks into place.
When we founded zkMe in late 2022, we saw a fundamental problem: web3 was hitting a ceiling. DeFi protocols wanted to serve institutional users but couldn't verify accredited investor status. RWA tokenization platforms needed compliance but couldn't sacrifice decentralization. Cross-chain bridges faced travel rule requirements for large transfers. Decentralized compute marketplaces like Akash and Render needed to ensure they weren't serving sanctioned entities.
Everyone was trying to bolt traditional KYC onto their applications, creating fragmented, centralized solutions that defeated the purpose of building on web3 in the first place. We realized the solution wasn't better application-layer KYC — it was identity as infrastructure: programmable, privacy-preserving, and composable.
That's what we've been building. A decentralized identity network that works across protocols, across chains, across use cases. X402 is the newest application of this infrastructure, but it's not the first. We've been working with DeFi protocols, RWA platforms, and compliance-focused dApps for years. What makes X402 special is that it's the first protocol designed from the ground up to be programmable and agent-friendly — which means it's the first protocol where our attestation infrastructure can show its full potential.
The machine economy isn't just another use case for us. It's the use case that proves why we built zkMe the way we did: as infrastructure, not as a product. As a protocol, not as a service. As a foundation that others can build on, not as a walled garden.
Looking Forward
CDP's roadmap for optional attestations is the right vision. It acknowledges that payment infrastructure and identity infrastructure are complementary layers that need to work together. We're excited to be the first attestation provider ready to plug into this ecosystem, and we're committed to keeping our infrastructure open and composable so that others can build on it too.
The machine economy is coming. Let's make sure it's built on a foundation we can all be proud of — one that balances innovation with responsibility, automation with accountability, and privacy with compliance.
If you're building on X402 and need attestation support, or if you're thinking about how to add compliance to your web3 service, we'd love to talk. The future of programmable commerce is being built right now, and we believe identity is the missing piece that makes it all work.
Reference
- X402 GitBook Documentation: https://x402.gitbook.io/x402
- X402 Official Website: https://www.x402.org/
- Coinbase CDP x402 Facilitator: https://docs.cdp.coinbase.com/x402/docs/facilitator
- zkMe Documentation Hub: https://docs.zk.me/zkme-dochub
- zkMe zkKYC Compliance Suite: https://docs.zk.me/zkme-dochub/verify-with-zkme-protocol/zkkyc-compliance-suite
- EIP-3009: Transfer With Authorization: https://eips.ethereum.org/EIPS/eip-3009
- EIP-712: Typed Structured Data Hashing and Signing: https://eips.ethereum.org/EIPS/eip-712





