Another week, another massive data breach. But this time, the numbers are so big they're almost hard to believe. Researchers just confirmed that 16 billion login credentials have been leaked—not from one company, but from pretty much everywhere you have an account. Apple, Facebook, Google, government services, you name it.
And here's the kicker: this isn't old recycled data from previous breaches. This is fresh stuff that hackers can actually use right now.

How Did We Get Here?
Let's be honest about what happened. These 16 billion credentials didn't leak because of some sophisticated cyber warfare. They came from infostealer malware and unsecured data stores. Translation: basic security screwups that any decent IT team should have prevented.
But companies keep making the same mistake. They collect massive amounts of user data, promise to keep it safe, then store it all in centralized databases that become irresistible targets for hackers. It's like putting all your valuables in one big safe and then being surprised when thieves try to crack it.
The crypto world figured this out years ago with the phrase "not your keys, not your coins." If you don't control your private keys, you don't really own your cryptocurrency. Well, it's time we applied the same logic to personal data: not your key, not your data.
The Root Problem: Centralized Data = Centralized Risk
Every time you complete a KYC process or create an account, your sensitive data gets stored in centralized databases—digital honeypots that become irresistible targets for attackers. The 16 billion password leak perfectly illustrates why the crypto community's mantra "not your keys, not your coins" needs an identity equivalent: "not your key, not your data."
When your personal information sits in someone else's database, you're not just trusting them with your data—you're trusting their security infrastructure, their employees, their protocols, and their ability to withstand sophisticated attacks. As this massive breach proves, that trust is often misplaced.
Why Traditional Identity Systems Keep Failing
The scale of this leak reveals three critical flaws in traditional identity management:
- Single Points of Failure: Centralized databases create massive attack surfaces. When they're compromised, millions of users suffer simultaneously.
- Data Ownership Illusion: Users think they control their data, but in reality, they're entirely dependent on third parties to protect it.
- Privacy vs. Compliance False Dilemma: Traditional systems force a choice between user privacy and regulatory compliance, when both should be achievable.
There's Actually a Better Way
Here's where things get interesting. What if platforms didn't need to store your personal data at all? What if you could prove you're over 21 without telling anyone your actual birthday? Or verify your citizenship without handing over your passport details?
This isn't science fiction— It's called zero-knowledge proof technology, and it's already working in the real world.
The idea is simple: instead of giving platforms your raw data for them to store and (inevitably) lose, you create cryptographic proofs that verify whatever they need to know. Want to prove you're old enough to use a platform? Your proof says "yes, this person is over 18" without revealing that you were born on 1995.
Why This Matters for Everyone
Zero-knowledge identity systems solve the core problem: they eliminate the need for centralized data storage. If platforms don't have your personal data sitting in their databases, hackers can't steal it in massive breaches.
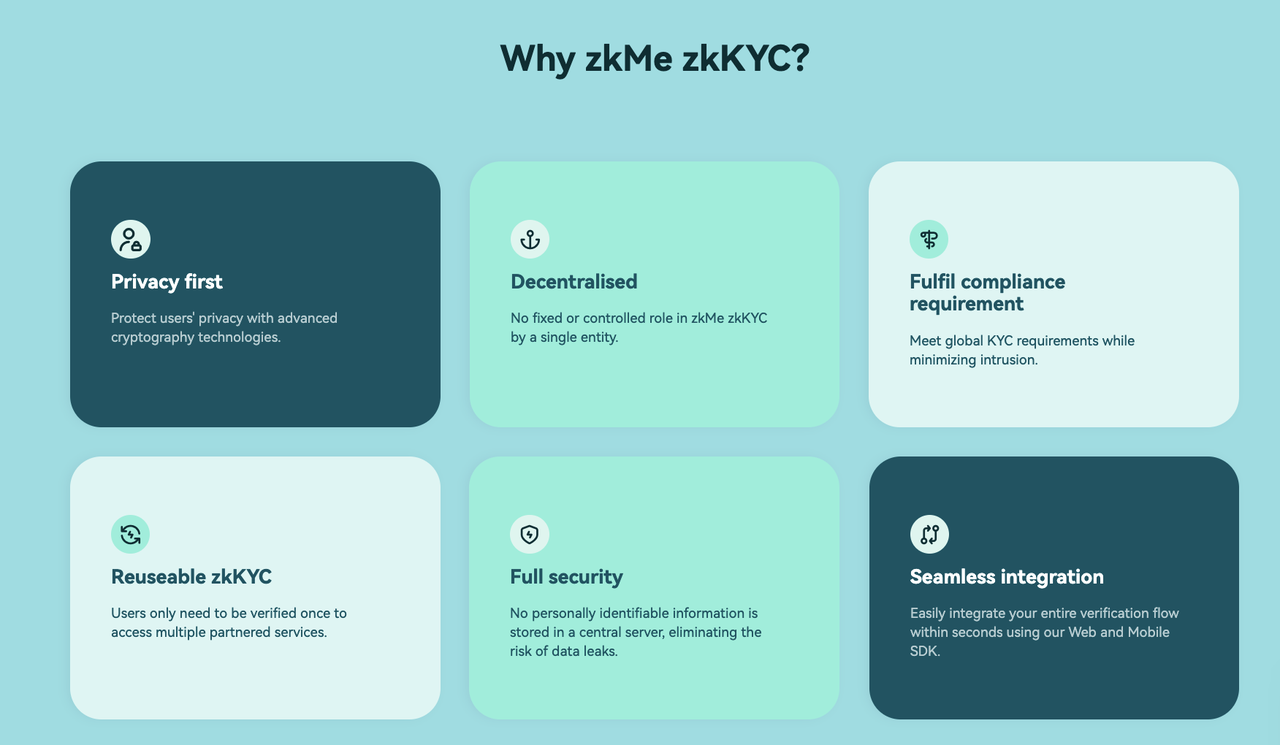
This isn't just theoretical. Leading platforms like Impossible Finance, CARV, and Alchemy Pay are already using zkMe's zkKYC solutions that let users verify their identities for regulatory compliance while keeping their personal information completely private. The results speak for themselves: streamlined compliance, enhanced security, and zero data breach risk. Users get the convenience of not having to re-verify their identity on every platform, and companies get compliance without the liability of storing sensitive data.
You don't have to choose between privacy and compliance. You can have both.
The Choice Is Pretty Clear
Look, more breaches are coming. That's just reality. But we don't have to keep playing this game where companies collect our data, promise to protect it, then apologize when they inevitably fail.
Zero-knowledge identity solutions exist today. The technology works, the implementations are live, and users are already benefiting from them. The only question is how long it'll take for the rest of the industry to catch up.
If you're tired of seeing your data in breach headlines, maybe it's time to check out platforms that don't store your data in the first place. You can learn more about zero-knowledge identity solutions at zk.me.
Data breaches will continue to happen. But they don't have to affect your users—if you act now.
About zkMe
⭐ zkMe builds web3 protocols and infrastructure for compliant, self-sovereign, and private verification of user credentials. The only web3-native solution for dApps to fulfill user due diligence (KYC) in zero-knowledge natively onchain, without compromises on the decentralization & privacy ethos of web3.
🔖 Use Cases: zkKYC, zk Credit Score, zk GPS Geoblocking, zk Investor Accreditation, Onchain AML, Anti-Bot/Sybil Protection.
🚀Trusted by over 80 projects and with over 1.5 million user credentials, backed by Multicoin Capital, OKX Ventures, Robot Ventures and more. zkMe is the leading onchain compliance provider.
For more information, follow the links below:
Website | Twitter | Discord | Telegram | Telegram Mini app |





